-
Home·Identity Theft·Identity Theft and the Hijacking of our Personal Information

What is Identity Theft?
When a person is born in the United States, he or she is first meaningfully (and sometimes quite uniquely) named by his or her parents or loved ones, and then inevitably numbered by the Social Security Administration. Ultimately, the number provided by our government is for the purpose of identification and tracking. This sophisticated method of tracking offers perpetrators the opportunity to commit acts of fraud by adopting the unique identifier of another and using that number for nefarious purposes. This is just one example of the growing problem(s) of identity theft and identity fraud. And it is one of the most common (and profitable) fraudulent acts perpetrated by criminals today.
Who is at Risk of Identity Fraud?
Identity theft can happen to anyone. Irrespective of race, nationality, gender, religious views, political affiliation, sexual orientation, or socioeconomic status, its victims can include the elderly and the newborn. It is an equal-opportunity hijacking. Even the mentally ill, infirm, and deceased are not safe. Our information is no longer secure; there is no longer such a thing as “privacy.”
This era of technology allows the digital pillager easy access to an individual’s personal information or a business establishment’s data to open fraudulent credit card accounts, apply for personal or business loans, or access financial records, subsequently allowing a thief the perfect silent opportunity to steal funds from their victims’ accounts. The damage is oftentimes done and the offender has gone long before the victim even realizes something has been taken.
The Role of Digital Science in the Battle
Digital science is extremely helpful in cybercrime. Digital forensics (also known as computer forensics) is a branch of forensic science. It deals with the investigation and recovery of material found on digital devices, often in relation to computer crimes or attacks. Private investigators who specialize in digital forensics can help apprehend the perpetrator by applying investigatory techniques to track activity using specialized techniques and software.

The average person is not privy to many of the programs to which the digital forensic specialist has access; therefore, it is ideal to hire a private investigator who specializes in this field to obtain evidence of fraud. Both civil and criminal matters use digital forensics to help those who have been victimized. Commercial organizations and companies can also use computer forensics to help assist within cases of intellectual property theft, forgeries, employment disputes, bankruptcy investigations, and fraud compliance.
The Consumer Sentinal Network
The Consumer Sentinel Network maintained by the Federal Trade Commission (FTC) tracks consumer fraud and identity theft complaints that have been filed with federal, state, and local law enforcement agencies and private organizations. In 2019, a record 3.2 million fraud and identity theft cases were reported. 1.7 million were fraud-related, approximately 900,000 were other consumer complaints and about 651,000 were identity theft complaints, according to the Insurance Information Institute, referenced in their 2019 Identity Fraud Study.
Warning Signs of Identity Theft
- Withdrawals from your bank account that you do not recognize.
- Not receiving bills and other mail.
- Checks suddenly become refused by merchants.
- Receiving calls from debt collectors regarding debts that do not belong to you.
- Your credit report shows unfamiliar accounts or charges.
- Receiving medical bills for services you did not render.
- Your healthcare provider rejects legitimate medical claims. Benefit limits show to be met, whenever they are in fact not.
- Medical records show that you have a condition that you do not have, of which your health plan refuses to cover.
- Notification by the IRS that you have more than one tax return filed in your name or declares that you work somewhere that you do not work.
- Receiving a notice that your information was compromised by a business that you have an account with or a data breach at an establishment where you do business.
What Steps Can I take to Help Protect Myself Against Identity Theft?
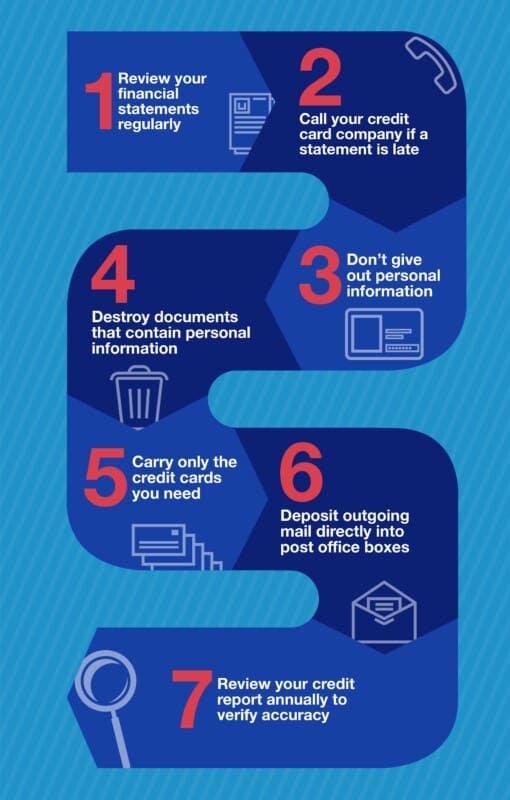
- Protect your Social Security card in a secure, fireproof lockbox. Never carry your Social Security card on your person. Verify the company upon request of Social Security number.
- Do not share personal information with non-verifiable sources. This includes your full legal name, social security number, birth date, or financial institute account numbers.
- Retrieve your mail every day. When you are away from your home or business for an extended amount of time, place a hold on your mail with your local post office.
- Reconcile banking and billing statements from your bank and credit card companies. If financial statements are delayed or don’t reach you, make sure you contact your bank.
- Utilize security features on devices, especially mobile electronics.
- While utilizing public wi-fi, use a private network (VPN), temporarily deactivate sharing capabilities, and update firewall settings.
- Financial institutions such as credit card companies, banks, or credit union statements need to be monitored. Look for unauthorized transactions on statements. Make sure to compare receipts with financial institution statements.
- To prevent “dumpster divers” from accessing personal information shred account/financial statements, credit offers expired credit/bank cards and receipts.
- Install protection software such as firewalls and virus-detection and prevention on all electronic devices.
- Create complex passwords to prevent thieves from guessing them and change them often. If a company that you conduct business with experiences a data breach, change your password immediately.
- Keep your passwords secure and unique. One of the most common sources of information for attackers is the use of a single password for many of your accounts. Apps such as 1Password, Lastpass, and Dashlane can help keep track of your passwords for all of the sites you use in a convenient, self-contained vault. All you have to keep track of is the account password and all. of your site-specific passwords are right there for your convenience. They also have browser extensions that can auto-fill your passwords right into the site so you don’t even have to go searching for it within the app.
- Review your credit reports either annually or semi-annually. Check for unfamiliar accounts. The Federal Government offers one annual credit report from all three reporting agencies at no cost.
- Contact credit bureaus and creditors such as Equifax, Experian, TransUnion, Innovis, National Consumer Telecommunications, and Utilities Exchange to freeze credit files at no cost. Credit freezes prevent thieves from fraudulently applying for and receiving approval for a credit account or utility service in your name.
Where Can I Turn for Identity Theft Help?
The risk of identity theft and fraud exists ubiquitously, especially with regard to digital technology. Still, the same technological advances equally combat this highly personable threat. Therefore, identity theft is both perceptible and largely preventable. One proactive measure is to utilize software services that offer identity theft protection. There are many programs offering identity theft protection to those who wish to increase their security. One popular solution is LifeLock. Another is Identity Guard. Yet another is McAfee (yes, that McAfee, the antivirus guys). For a list of possible solutions, you can also visit Consumers Advocate.

Make sure to perform credit checks frequently. This allows individuals to continuously monitor activity corresponding to one’s social security number. If you have been (or think you have been) a victim of identity theft and need to file a report, please visit the Federal Trade Commission and report your claim. You will have the opportunity to create a personalized recovery plan. The recovery plan consists of a step-by-step recovery process that puts your plan into action, updates your plan as needed, tracks your progress, as well as offers prefilled forms and letters for the advancement of your recovery.
Conclusion
To summarize, individuals and businesses alike need to create an attentive internal system that thoroughly prevents and protects personal, consumer, and business information.
If you suspect that you have been targeted for identity theft or fraud, quickly act by checking credit reports for unauthorized or unfamiliar accounts. If one finds evidence to pursue further investigation, freeze your credit and report the incident to appropriate authorities. Another important safeguard is to employ a digital forensic investigator to trace virtual activity. Ultimately this will be in one’s best interest in helping to minimize the damage and gain evidence if legal action is available.
It never feels good to experience a violation of any sort. Although identity theft is a concerning threat in today’s technological era, taking the steps necessary to protect yourself and your family, as well as your business, employees, and consumers by maintaining a proactive stance can provide one with sound peace of mind.
The Private Investigation Gear We Use
We are excited to announce that this article has been published by Pursuit Magazine! Check out the published version.
Gear is a very important part of any private investigator’s toolbox. The tools of our trade are usually pretty high-tech and oftentimes quite expensive. Private investigators are usually very opinionated on gear and we can talk about it nonstop if you let us (and sometimes even if you don’t). We are very vocal in our support of one brand or another and whether this will help us get evidence better or that will allow us to be just a wee bit sneakier. However, ultimately the investigation equipment we choose needs to accomplish three things: it needs to be useful, it needs to be durable, and it needs to be high-quality. If it makes us feel more covert and look super-cool in the process, all the better.
What Investigation Gear Do We Use on the Regular?
This is a list of our favorite indispensable pieces of private investigation gear we use while on surveillance:
- Camcorder – Our camcorder of choice is the Panasonic HC-V770 (~$499). It is a full-HD camcorder with a wide range of available accessories. It has a 20x optical zoom and 50x digital zoom. We want the most optical zoom we can get and this camera doesn’t disappoint. Between optical and digital, always go with the most optical zoom you can afford. Optical zoom is a measure of the physical movement of the lens, whereas digital zoom is some kind of internal software wizardry that usually ends up pixellating the image if you take it too far. The more optical zoom, the better. Don’t go for the 4K version (the HC-VX981K). It’s overkill and will needlessly chew through your memory card.
- Tripod – The Sirui 3T-35K Plus is a very good all-in-one. This baby can act as a monopod or a self-standing tripod. It comes with a ball head for adjusting the angle as well as an extension bar to give you a little more height. The three extending “feet” lock in place and give you a firm and flat support for your camera or camcorder. The legs can also fold in, turning the device into a very functional monopod. We do wish it were a bit taller, as we find that we have to either hold it or rest it on our thigh to give it the reach it needs to hold the camera high enough to see out the window. But, that’s really the only complaint. It’s built like a tank and feels very well-made.
- Dropcam – A dropcam is a small, battery-powered camera that can be hidden in a particular location and keeps an eye out while (hopefully) remaining undetected. They are motion-activated and, like a trail cam, will start recording when they sense something moving within their field of view. We usually use them in hotel hallways or lobbies to catch people going into or leaving hotel rooms with people they aren’t supposed to be with, etc. There are two types: rotating and fixed. The rotating type (~$125) is a small camera (much smaller than your cell phone) that has a small rotating head on it where the lens is located. This allows us to place it somewhere and rotate the head on an angle to specify where we want the camera to look. The fixed type (~$130) is slightly larger but doesn’t rotate. It does, however, have night vision, and we LOVE night vision!
- Keychain Camera – If we need to leave the safety and comfort of our cars and follow someone into a particular location, we need a video camera that is virtually undetectable. This one does the job. This is a camera that is disguised as a key fob. We put it on our keyrings and it looks exactly like that thing you use to unlock your car. Trust me, you can’t tell the difference. We can put it on a table or hold it in our hands while we follow a subject into the mall or the grocery store and get every move they make in public. It takes both video and still photographs. It’s actually kinda unnerving that these things exist, but we use them all the time. We like the Lawmate PV-RC200HD2 (~$300).
- Dashcam – This one is really more for our safety. Much like police dashcams that keep them honest and record any altercations that may take place, we use a dashcam for much the same reason. If we are following a subject in our vehicle and there is an altercation with a subject (they do happen), then we want everything on record. Not only does it help us should we need to go to trial, but it can also help law enforcement investigate should the unthinkable happen. Vantrue makes excellent dashcams and is the brand we chose. For our surveillance vehicles, we went with the Vantrue X4 UHD (~$179). This one IS 4K and for good reason. It records on a loop and gets very fine detail within a wide field of view. This can also help us document the location where we lost a subject, should that happen (*hangs head*). Oh, and this one has night vision, also!
- Binoculars – This one should be obvious. The closer we get to the person we are watching, the more likely we are to get spotted (“burned”), which would ruin the investigation. Therefore, we try to do everything we can to sit as far away from our subject as possible. Therefore, we need a pair of binoculars handy to zoom in and watch a location from afar. Many investigators simply use the zoom feature on their camcorders, but we feel that it is better to maintain our camera on a fixed position of interest and do the majority of our surveillance through the lens of a good pair of binoculars. We chose the Nikon Monarch 5 (~$325) and have no complaints whatsoever. It has a 12x zoom and is waterproof, fog-proof, and has a rubberized body in case you fumble and it gets away from you.
- Portable Power – We have to keep all of this gear powered up and running. Therefore, for longer surveillance jobs, we have to carry our power with us. We can’t always start our car and use the vehicle’s power adaptor. So, we need battery-powered capabilities. For strict battery power, we chose the Anker PowerCore 20100mAh (~$45 each) with 4.8V output and we carry at least two of them with us at all times. There is nothing worse than having the goods in your sights and having your battery go kaput on you. We have backups of our backups and everything is always fully-charged when we walk out of the office. Clients don’t want to hear that you missed out on the evidence they need because you were too careless to make sure you had juice when you needed it. These are invaluable and, in actuality, we will probably end up getting a couple more. If we are able to keep our vehicle running, then a power inverter can be a lifesaver. This can keep your phone, iPad, computer, etc. all charged and ready to go. The Bestek 300W 4.2V power inverter (~$35) is what we chose and it’s very nice. It comes with two 110V plugs and two USB charging ports.
- Air Compressor/Battery Jumpstarter – You know the saying, “S**t happens?” Murphy rules the road when you are 300 miles from home and all alone at 3 am in the middle of nowhere and you can’t get a signal on your phone to call AAA when your battery dies from charging all this cool crap. Well, Pilgrim, if you have the Clore Jump-n-Carry JNCAIR 1700 (~$230) with you, then you can consider your bacon saved. This thing has an integrated air compressor and battery charger in it that can get you back on the road like it never happened. No need for a second vehicle to jump you. It is completely self-contained. If you have a flat and your tire is beyond saving (i.e., blowout, etc.) make sure to always have a spare tire, jack, flashlight, and flares on hand to repair any flats along the way.
- Tablet – This one seems to be on everyone’s list lately and is self-explanatory. We go paperless when we can and, these days, a tablet is simply a must. You could use your cell phone, but if you have your GPS up and a call comes through while you’re trying to check an address change the client just gave you, etc, etc, etc, it helps to have something else to go to with this stuff. Plus, note-taking apps, such as Notability, can help you keep all your pertinent information right there in front of your face so you don’t have to go looking for it. This allows us to keep our phones free and not get tangled up in multi-tasking on a single device. We also have our CROSStrax case management app up so that we can keep any case-related information handy, as well as edit the master case file as we go.
- Digital Camera – Honestly, we will probably get roasted by our colleagues for this, but we really don’t use the digital camera all that much. The cameras on cell phones these days are more than adequate for time/date stamp photos and to snap a pic of an address or a vehicle or someone coming in or out of somewhere. In all honesty, we use the camera on our cell phone way more than we do the digital camera. However, every once in a while, when we need a lot of zoom on a still image and don’t think the evidence would be better suited in video format, we will whip out our Nikon CoolPix 950 and use that sweet, sweet 83x optical zoom to snap a quick pic or two of what we see. But, 90% of the time, we either get it on video (camcorder) or we just use our iPhones.
And Now for the Stuff We WISH We Had (or could afford):
- A DRONE! – Man-oh-man, do I wish I had a drone.
- SiOnyx Aurora Night Vision Camcorder – Again, NIGHT VISION! And this baby does it in FULL COLOR!!
- Rode RODECaster PRO Podcast Production Studio – The creme de la creme of outboard podcasting sound engineering and I want one!
- Zoom H6 6-track Portable Recorder – Podcast from anywhere? Yes, Please!
- DefCon Countermeasure Sweep Equipment – DefCon makes excellent countermeasure sweep equipment, but they are PRICEY! One day, if the demand is there, we will upgrade. DD1206, PRO-10G, DD802, and the crown jewel DD1207!
And that’s it! This pretty much sums up the private investigation gear and equipment we use every day and shows a few of the things on our wishlist. If you are in the biz, do you agree or disagree with our suggestions? Leave a comment down below if you use some of the same things we do or if you think what you use is better.

Shaun is the owner of Red Door Investigations. He has a Ph.D. in psychology from the University of Texas at Arlington and is a licensed pilot and certified scuba instructor.
What Can a Private Investigator Do?
Ever wonder what things a private investigator can do that are legal during the course of an investigation? Here is a list of five things that a private investigator can do, along with some common misconceptions and best practices. For each item in this list, we will discuss some of the things we are allowed to do legally, a common misconception about this allowance, and why this misconception is incorrect. For a list of what we are NOT legally allowed to do, check out the upcoming companion piece to this one, Five Things a Private Investigator CAN NOT Do Under Any Circumstance.
1. As long as we aren’t on private property, a private investigator can sit outside of your house or workplace and watch everything you do.

This doesn’t mean you shouldn’t be vigilant about strange or suspicious vehicles parked on your street. If you see a vehicle that you feel doesn’t belong there, please call the police. The police will question the individual and make sure they have a legitimate reason for being there. And if not, they will force the person to leave.
MISCONCEPTION: I have to authorize any picture or video taken of me.
2. We can follow you wherever you go and record everything you do there (yes, even that).

This is kind of a corollary to #1 above, but I wanted to re-iterate it again. If we can “see” you from where we are on public property, you are fair game. Be VERY careful about what you do in public. We are very sneaky and have all kinds of high-tech sorcery that allow us to blend in and appear bland and nondescript. Forget the fedora, trenchcoat, and magnifying glass. We make our livings out of blending in and not drawing attention to ourselves. Again, if you notice we are there, we have failed.
MISCONCEPTION: If I am in my car, then what I do is private.
Negative. We can’t ENTER your vehicle (obviously), but your car has windows and we can see through those windows just like you can. If we can SEE it from public property, then we can RECORD it from public property. I’ll say it again for the people in the back: BE VERY CAREFUL WHAT YOU DO IN PUBLIC! If you don’t want to see yourself on video in a court of law one day or you are doing something you wouldn’t want your spouse to know about, think twice before doing it anywhere in public. Think twice before doing it at all, but you get my point.
3. We can go through your garbage.

This one surprises a lot of folks. Destroy/shred/whatever anything you don’t want to be recorded, gone through, and shown to a judge/jury, your insurance company, or your spouse. Don’t throw away your bank statements, telephone records, or the receipts you used to take your mistress out on the town. Destroy them. Even shredding has its limitations and a highly skilled and resourceful private investigator can piece them back together again.
There is one caveat, though: we can’t touch it, look at it, open it, etc. until you set it out to be collected by the city. Trespassing laws are pretty strict and until you set it out on the street to be collected, it’s still on your property and we can’t touch it. We can, however, watch your property and scoop it up as soon as you set it out for the garbage man.
MISCONCEPTION: Because my trash is mine, it’s private and it’s safe from prying eyes.
Wrong. Once you set it out to be collected, it becomes public property and we are well within the law to drive right up to your curb, throw it in our vehicle, and speed off without you even knowing it’s been done. We just saved the garbage man a stop and your trash is now a treasure trove of useful information. Fans of the television show Columbo should know this was a favorite tactic of the famous detective. He always went through the trash. It can be a gold mine.
This is mainly because people aren’t careful about what they throw away. The trash is actually one of the worst places you can dispose of sensitive documents or information. Think before you throw anything away. There are many people who realize the potential in your garbage. Not only can private investigators use it for evidence, but it can also be a treasure trove for identity thieves.
Also, don’t set your trash out “the night before.” Wait until the morning of pickup to set out your trash and do it as close to pick up time as you can. This will minimize the window of time that thieves and others (we) have to scoop it up. If it’s out there all night while the whole world is asleep, then you’re just asking for it to end up on a table somewhere and poked through.
4. We can lie…to you, your family, and your acquaintances (NOT our clients, though)
This is given the fancy-sounding name “pretexting.” Whatever you call it, it’s basically lying and this right here is one of the many reasons private investigators have kind of a “shady” reputation with the general public. A pretext is a gambit designed to do one thing, trick you (or those who know you) into giving us information. And in this game, information is everything. Private investigators are in the information-gathering business. It’s what we do.

We can call, text, DM, etc. your family, your job, your neighbors, etc. and social engineer them in a way that sets them off guard and pushes them to inadvertently help us get information on you. Social engineering is essentially tricking someone into giving out information they wouldn’t normally divulge. It takes many forms and can be used for all kinds of nefarious practices by people with less-than-legal (or moral/ethical) intentions, but private investigators use it legally all the time. And your social media accounts make this almost effortless. It’s one of the first places we look. Pay very close attention to what you post online and what you allow others to “tag” you in, especially pictures. We have closed many cases of infidelity without even leaving the office simply by scouring social media and downloading pictures of the subject all smoochy-smoochy with someone who is not the spouse or significant other.
There are a couple things we can NOT do within this arena. We can’t misrepresent ourselves as law enforcement or a representative of a real-life company. That’s a big no-no. We also can’t misrepresent ourselves as a real person to get private information on that person. A private investigator can’t call your bank and pretend to be you in order to get information about your account, for example. It’s also a legally grey area to use pretext when a subject is represented by counsel in pending litigation. This can potentially land the private investigator in trouble with the court and that investigator could find him or herself at the business end of a TRO and/or harassment suit.
But, we can certainly be your “long-lost classmate” who is looking for you so we can get your address for our upcoming class reunion, we can be an “old college buddy” from back in the day who is inviting people to the wedding of someone we know you have in common, or we can pretend to have something of value that you “dropped on the subway” and we would very much like to return it, if only we knew where you work so we could drop it off, etc. It sounds hokey and like something that would never work, but you’d be surprised at the information you can get if you ask for it the right way.
MISCONCEPTION: Any evidence gained via pretext or misdirection is inadmissible in court.
Wrong again. This is a common misconception spread by television and movies. Much like a police officer doesn’t have to tell you they are a police officer if you point-blank ask them (this is also a myth), a private investigator does not (and never would) disclose who they are during a pretext scenario. This would invalidate the entire reasoning behind the endeavor. We want the information, and as long as we don’t misrepresent ourselves as law enforcement or the representative of a real-life company (see above), then we can misdirect and set off-guard anyone we think can point us in the right direction.
5. We can use any public record available in order to deliver the most complete package of information to our clients.
Private investigators have access to all kinds of juicy information about you. You’d be awestruck at the sheer volume of information about you that is floating around in the world. Edward Snowden didn’t even scratch the surface of the surface. Everything you do online is cataloged and databased and essentially sold to the highest bidder under the context of “advertising.”
Everything.
There are a few things we (or anyone else) aren’t privy to. For example, medical (HIPAA) and financial records are off-limits and protected by the federal government. Interestingly, so are educational credentials (FERPA). We can’t get your college transcripts, your bank records, or the results from your most recent doctor’s appointment. But pretty much everything else is available for the taking for someone who is crafty and knowledgeable enough to know where to find it. This skill oftentimes goes by the moniker OSINT (Open-Source INTelligence) and is a service we offer to our clients, both outbound (gathering outside information on another person) and inbound (shedding light on their own vulnerabilities).

MISCONCEPTION: My information is private and protected and companies have my best interests in mind when they collect it.
Ha! That’s funny. I hope you’re starting to notice a pattern here. There is no more privacy in the digital world. For someone who is motivated enough, any information about you can be gotten with enough determination and skill. You’ve read the horror stories about identity theft and corporate hacking centered on the release of the personal data of thousands (or even millions) of unsuspecting and trusting individuals. These are real. Your information is NOT safe. Just do the best you can, cross your fingers, and hope for the best. There are a few things you can do to protect yourself and minimize your risk, but that is far outside the scope of this article.
Just know that your data is out there and it’s never coming back. Be very careful who you allow to have access to your information and check your passwords and privacy settings often. It’s the wild west out there.
Conclusion
So, that was five things that private investigators are legally allowed to do. There are many more, of course, and we will discuss those in a future post. Many of the laws governing private investigators are state-specific and what is allowed in one state may be banned in another (recording phone conversations, for example). But this list is pretty inclusive. Most of the private investigators licensed and working in the US today are able to (at a minimum) do the things outlined in this list. And it’s all perfectly legal.
Check out our next post where we will discuss some of the many things private investigators CAN NOT do, under any circumstances.

Shaun is the owner of Red Door Investigations. He has a Ph.D. in psychology from the University of Texas at Arlington and is a licensed pilot and certified scuba instructor.
Can Relationships Overcome Infidelity?
Infidelity and cheating are viable threats to any intimate relationship. Predicaments of an affair are a possibility for anyone, especially during this era of technology and virtual anonymity. Betrayals of relationship integrity, whether through infidelity, cheating, or adultery are, unfortunately, more common than one would think. If the couple has children, the fallout can be even more devastating. The following statistics help to illustrate the possibility of adultery occurring in one’s relationship:
- 40% of unmarried couples and 25% of married couples experience at least one incident of infidelity or cheating at some point within the relationship.
- 70% of all Americans engage in an affair of one type or another at some point in their marital life.
- 45% of men and 35% of women have been either sexually or emotionally intimate with someone other than their committed partner.
- 45-50 % of married women and 50-60% of married men engage in extramarital affairs at some point in their relationships.
That Sounds Bad! Is My Relationship Doomed?
No, but it will take some work. It may seem hopeless to repair a relationship that has been damaged by one of the ultimate betrayals. Cheating is the one error in judgment that is considered to be a deal-breaker for most relationships. Trust is a necessity in all aspects of relationships. It stands to reason, therefore, that a violation of trust, such as infidelity and cheating, can cause great heartache and devastation within a marriage. Infidelity can undermine the bedrock and the very foundation of marriage itself. It can devastate, humiliate, and crumble a once-thriving and loving union.
However, with hard work and a resolved commitment to make the relationship succeed, many relationships can (and do) survive a bout of infidelity or cheating. Just because your partner shows signs of cheating does not mean they are being unfaithful. And, even if your partner is cheating, an instance of infidelity doesn’t mean that your marriage is doomed. Marriage and family therapist Gabrielle Applebury states “adultery is no longer a deal-breaker in many marriages,” and that “70 percent of couples actually stay together after an affair is discovered.”
It takes time, patience, and commitment to overcome this obstacle. Relationship advice author Kevin Darné said, “one of the most important things a betrayed person should do is take some time to determine if they really can forgive.” When both partners are committed to healing the damage and closing the gap caused by a significant breach of trust, many marriages do survive and, with concentrated effort and work, can actually become stronger and experience deeper levels of intimacy.
The Three Types of Intimacy
There are three specific tools to “affair-proof” your relationship: Self Intimacy, Conflict Intimacy, and Affection Intimacy. These three tools can be thought of as the mortar to the building blocks of any relationship. Every recipe for a long-term relationship has at least some of each of these three ingredients.
Self-Intimacy
To start, self-intimacy is knowing what you feel, think, and want, and sharing these with your partner. It is being self-aware. When we are self-aware, we acknowledge what motivates us so that we can make healthier, more mature choices. We use our Emotional Self Awareness to strengthen Self Intimacy. Emotional intimacy is the foundation of any solid relationship. “Emotional intimacy can be defined as allowing yourself to connect more deeply with your partner through actions that express feelings, vulnerabilities, and trust”, says Sanam Hafeez, a neuropsychologist in New York City and faculty member at Colombia University. It is being open and vulnerable and expressing that vulnerability to your partner. This brings couples closer together and enhances overall trust. And overall trust enhances intimacy.
Conflict Intimacy
Secondly, conflict intimacy is the ability to “do conflict well” in a relationship. This is a key tool that many couples lack. Differences and tension are inevitable in all relationships, especially those weathering infidelity, and being able to talk about these with one another is essential. Conflict intimacy is a marker of how well the couple can overcome tensions and difficulties within the relationship. The more effectively a couple can handle stress and tough times, the stronger and closer that couple is. Being able to “argue well” is a good indicator of how strong your relationship is. When couples can talk with respect and calm, they can begin the process of working through the negative, while simultaneously remaining in touch with the positive, loving aspects of their relationships.
Affection Intimacy
And finally, affection intimacy is the “gravy” in the relationship; it is the sweet, sensual, and passionate/sexual aspects of the relationship. It feeds the love that grew early in the courtship. When a couple is good at Self Intimacy and Conflict Intimacy, their Affection Intimacy grows and flourishes. Their relationship is resilient and can handle differences. More importantly, they have a way of constructively dealing with the inevitable challenges that happen in all relationships. In this context, relationships with high levels of affection intimacy are able to discuss issues of personal integrity. Subsequently, they are better prepared to weather risks to relationship integrity. They are able to present fears and vulnerabilities in a way that does not harbor insecurities or view secrets as acceptable.
The Need for “Love” and the Influence of Commitment Phobia
We are all human. We cannot simply turn off our biological urges and ignore our instincts. However, we ARE able to control our behavior and not give in to our darkest desires. Unfortunately, many of us do succumb to this desire, especially during a vulnerable time in our life. It is very important that we maintain healthy communication within our relationships. We must do this with consistency, respect, understanding, and kindness.
Ultimately, human beings are social creatures; we all crave connection and unity with other people. In relationships that do not meet this need, it can be easy for one to stray. For some, it’s difficult to live up to the expectations of others. For others, commitment phobia and relationship anxiety are real and trying fears that can influence every relationship in their life. This is particularly true in romantic relations.
Some Common Causes of Commitment Phobia
Some common causes of commitment phobia can include:
- Worrying that the relationship will end without notice or signs.
- Fear of not being in the “right” relationship.
- Concern about being in an unhealthy relationship characterized by abandonment, infidelity, abuse, etc.
- Childhood trauma or abuse.
- Unmet childhood needs or attachment issues.
- Complicated family dynamics while growing up
For these reasons, some relationships are especially challenging to preserve, and cheating can result from some of these unresolved issues. Inevitably, not every relationship can withstand the transgression of an affair. Therefore, the unity and intimacy that once thrived in a healthy relationship can become extinguished and a single act of betrayal can develop into a casualty of the marriage.
What Happens if the Cheater Decides to Leave His or Her Spouse and Marry the Outsider?
Well, statistics are not in their favor. For instance, roughly 3% of men who engage in extramarital affairs marry their mistresses. Men who do marry their paramours have a subsequent divorce rate as high as 75%. In fairness, most second and third marriages fail regardless of why the first one ended. A couple beginning their relationship on the betrayal of a sacred vow may have the odds stacked against them. But a marriage constructed out of unconditional love can overcome many obstacles, including infidelity.
What Are the Next Steps if My Partner Has Cheated?
For couples wishing to repair a marriage upended by infidelity, carefully consider how to proceed. Before choosing to decide whether to stay together or go your separate ways, take the time to heal and understand what was behind the affair. This is not a time to make important family decisions based on emotional responses. A marriage constructed out of unconditional love can overcome many obstacles, but there is also honor in fighting for your vows. In this, honor can heal wounded hearts. The following are significant tools that one may choose to apply in the healing process of their marriage:
- First, seek guidance from a licensed psychologist and/or certified counselor who specializes in marriage and family therapy. Within these sessions, remain focused on the marital problems that built up to the affair. Do not stray away from the underlying problems. Find a therapist that encourages both parties to take accountability, this is imperative. Stay within boundaries. This is not the time to bring up any topics that existed prior to the relationship, such as childhood issues or any comparison of your current partner to those of previous relationships. A good marriage counselor will help you put the affair into perspective and help to identify the contributing factors that led to the affair. He or she can further provide both parties with the tools to rebuild and strengthen the relationship.
- Second, seek help from outside sources such as spiritual leaders, understanding and non-judgmental friends, and reading material that relates to infidelity. You may also consider utilizing resources on any of the issues that contributed to the affair. For example, self-help books, educational materials focusing on issues regarding control, and/or abusive tendencies within the relationship (if applicable) could be beneficial.
- Third, if outside influences played a part in the damage that accrued, such as sexual assault, then other sources of help or information are available. If sexual assault is a factor, then other, more pressing issues of grieving come into play. Educating yourself on the sensitive topic of sexual assault, as well as the effects and aftermath, can help you and your partner overcome this trauma. Take the time to learn how to support your partner in healing from a traumatic situation. The support will certainly enhance the healing process and forge a strong bond to move forward with further reconciliation. “The only effort earned is the effort received. You get what you give, so give it your all.” Attitude is everything in life, thus it is important to reflect positive vibes with a mentality of “I’m willing to do everything I can to make this work.”
- Finally, create a plan to re-establish trust, with the goal being reconciliation. If you were the responsible party and the betrayal is yours, admit your disloyalty to your partner, hold yourself accountable, and seek authentic forgiveness. If it was your partner who committed the infidelity, offer forgiveness when you are truly ready and seek understanding and reconciliation with the helpful tools described above.
Concluding Thoughts
You should never consider an act of retaliation by cheating on your partner in kind. The healing process necessitates that both parties work to regain lost trust and respect. Moving forward will probably get worse before it gets better. It can be done, but only if both parties are committed to healing the relationship, despite all the pain and suffering that both parties are feeling. If you can work together and stick it out, the results can be very rewarding. Subsequently, one can achieve a renewed marriage–a partnership that continuously flourishes and will likely exceed any previous expectations and emerge renewed. Ultimately, to move forward successfully, reconciliation must be the end goal for both partners.

